TORRANCE, Calif., Dec. 19, 2025 (GLOBE NEWSWIRE) -- Criminal IP (criminalip.io), the AI-powered threat intelligence and attack surface monitoring platform developed by AI SPERA, is now officially integrated into Palo Alto Networks’ Cortex XSOAR. The integration embeds real-time external threat context, exposure intelligence, and automated multi-stage scanning directly into Cortex XSOAR’s orchestration engine, giving security teams higher incident accuracy and faster response than conventional log-centric approaches.
For Palo Alto Networks, widely regarded as the global leader in cybersecurity, Cortex XSOAR is a central hub for SOC automation. With Criminal IP added as an integration through the Cortex Marketplace, Cortex XSOAR can now offer users the ability to evaluate suspicious IPs and domains not only through static reputation data but also through behavioral signals, exposure history, infrastructure correlations, and AI-driven threat scoring, without requiring additional systems or analyst-driven lookups.
AI Context to Address the Limits of Log-Only Incident Response
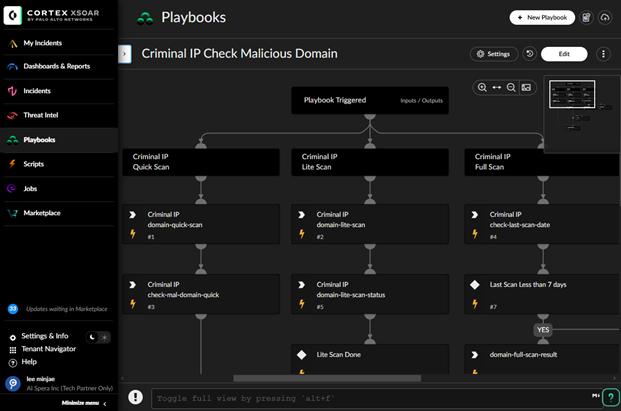
Automated playbook example — detecting malicious domains using the three-step scan in the integrated API of Criminal IP and Palo Alto Networks Cortex XSOAR
Modern SOC teams face overwhelming alert volumes, yet traditional enrichment still depends on static reputation feeds with limited context, often missing port exposure, CVE ties, certificate reuse, DNS changes, or anonymization behavior. Criminal IP fills this gap by continuously analyzing global internet-facing assets and correlating IP behavior, domain activity, SSL/TLS data, port states, CVE exposure, IDS hits, and masking indicators. When an alert includes an IP or domain, Cortex XSOAR can automatically pull this enriched intelligence into the active incident via a playbook, allowing analysts to assess intent and severity without leaving Cortex XSOAR.
Multi-Stage Scanning and External Exposure Linking
Cortex XSOAR playbooks can trigger Criminal IP’s automated three-stage scanning workflow: beginning with a Quick Lookup, escalating to a Lite Scan, and then performing a Full Scan for complete attack surface analysis. Full Scan results are delivered as structured reports within Cortex XSOAR, with generic polling ensuring the workflow continues without manual effort. Beyond alert-driven enrichment, the integration also links internal telemetry with open-internet intelligence providing historical behavior, C2 relationships, anonymization indicators, abuse records, and SSL correlations for each indicator. Cortex XSOAR can also schedule Micro Attack Surface Management scans to assess exposed ports, certificate validity, vulnerable services, and outdated software, offering lightweight, continuous ASM capabilities that help organizations identify weaknesses before they are exploited.
Accelerating the Shift Toward Intelligence-Driven Autonomous Security
Screenshot of the Criminal IP pack on the Cortex Marketplace
The integration between Palo Alto Networks and Criminal IP reflects a broader trend toward autonomous security operations. By combining Cortex XSOAR’s automation and orchestration capabilities with Criminal IP’s real-time external analysis, SOC teams can automate decisions that previously required manual research across multiple intelligence sources. This reduces response times, improves the accuracy of incident classification, and minimizes analyst fatigue—issues that have grown more severe as alert volumes and AI-generated threats continue to rise.
Criminal IP is already present on Azure, AWS, and Snowflake marketplaces and maintains integrations with more than 40 security vendors, including Cisco, Fortinet, and Tenable. Its expansion into the Palo Alto Networks ecosystem sets the foundation for further integrations across XDR and cloud security solutions.
AI SPERA CEO Byungtak Kang stated that the integration “demonstrates the growing importance of AI-driven threat intelligence and exposure analytics in enterprise security operations,” adding that Criminal IP aims to play a central role in helping organizations transition toward fully autonomous defense architectures.
About Criminal IP
Criminal IP is the flagship cyber threat intelligence platform developed by AI SPERA. The platform is used in more than 150 countries and provides comprehensive threat visibility through enterprise security solutions such as Criminal IP ASM and Criminal IP FDS.
Criminal IP continues to strengthen its global ecosystem through strategic partnerships with Cisco, VirusTotal and Quad9. The platform’s threat data is also available through major US data warehouse marketplaces including Amazon Web Services (AWS), Microsoft Azure and Snowflake. This expansion improves global access to high quality threat intelligence from Criminal IP.
Users can learn more: https://cortex.marketplace.pan.dev/marketplace/...


